
Automation, Control & Plant Intelligence - Articles, Analysis, Reviews, Interviews & Views

 Security Techniques Using Off-the-Shelf Products
Security Techniques Using Off-the-Shelf Products
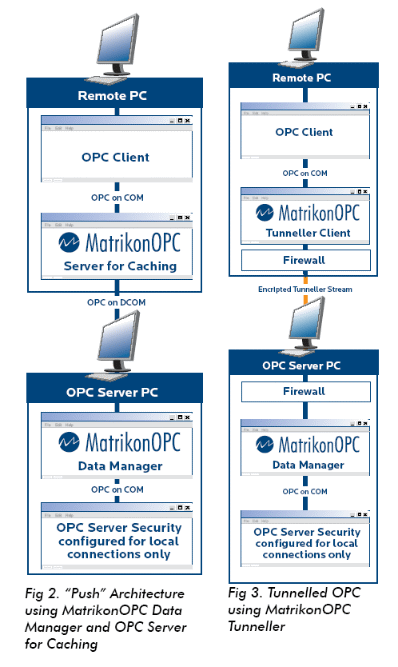
 lock the data stream between OPC Client and OPC Server, encrypt the tunneled data and configure the server to
only allow tunneled connections from the OPC Client’s IP address. Matrikon’s OPC Tunneller enables data stream encryption and only allows access from OPC Client’s
you specify. In my opinion this architecture represents the
best in layered security for OPC systems because it removes
DCOM from the equation and allows use of firewalls on all PC’s. Tunneled OPC makes OPC over the internet possible without VPN connections and their associated security configuration. Unlike XML-DA, OPC tunneled with Matrikon’s OPC Tunneller does not take a significant performance hit.
lock the data stream between OPC Client and OPC Server, encrypt the tunneled data and configure the server to
only allow tunneled connections from the OPC Client’s IP address. Matrikon’s OPC Tunneller enables data stream encryption and only allows access from OPC Client’s
you specify. In my opinion this architecture represents the
best in layered security for OPC systems because it removes
DCOM from the equation and allows use of firewalls on all PC’s. Tunneled OPC makes OPC over the internet possible without VPN connections and their associated security configuration. Unlike XML-DA, OPC tunneled with Matrikon’s OPC Tunneller does not take a significant performance hit.
YOU MAY LIKE:
Popular Articles
Manufacturing Insights